Real-Time Vaultless & Keyless Tokenization
Instant Data Protection for Payments and Financial Transactions
Meet global compliance standards in as little as one week.

No Keys
No Vaults
No Latency
No Hardware
No Downtime
Our Partners











What Is Vaultless, Keyless Tokenization?
Vaultless, keyless tokenization replaces sensitive financial data with irreversible tokens in real time, without storing data or managing encryption keys. This enables secure, high-speed transactions while reducing compliance scope and breach risk.
How Vaultless Tokenization Works
A modern, stateless architecture designed without centralized storage or lookup tables. Unlike traditional vault-based approaches, Rixon removes long-term exposure by design while keeping systems fully functional.
Rixon's 3-Step Flow
1
Data Enters
Sensitive data is captured securely through your API endpoints, applications, or payment workflows.
2
Tokenized Instantly
Irreversible, keyless, vaultless, and no original data stored in Rixon's systems in exploitable form.
3
Detokenized on Demand
Original data is retrieved only under strict roles, logs, regions, devices, or times.
Advanced Security Features
Stateless, Key-Free Architecture by Design
Cloud-Native, Auto-Scaling, and 99.999% Uptime
AI and ML Monitoring and Anomaly Detection
In-Region Compliance (GDPR, LGPD, APPI, DPDP)
Rixon’s vaultless, keyless tokenization is not encryption or format-preserving encryption (FPE), and does not rely on stored vaults or encryption keys.
Protect Payment and Card Data with Zero Stored Risk
High-Speed, High-Savings Protection
Reduce Fraud and Risk
Keep sensitive data out of your systems so attackers have nothing to target.
- Reduces fraud risk by minimizing stored sensitive payment data
- Eliminates vaults and keys that create breach risk
- Adds real-time monitoring and strict access controls
Simplify Compliance
Remove sensitive data from your systems to make compliance simpler.
- Supports PCI, GDPR, LGPD, APPI and DPDP requirements
- Region-bound access meets global sovereignty rules
- Clear audit trails make assessments faster and predictable
Boost Global Performance
Keep transactions fast and stable, even during peak global traffic.
- No vault lookups, no persistence or key rotation
- Autoscaling keeps transactions fast everywhere
- Designed to support emerging payment flows and A2A networks
Cut Internal Costs
Remove legacy systems so your architecture stays modern and efficient.
- No vaults, HSMs or key lifecycle tools to manage internally
- Less infrastructure to maintain across environments
- Reduces long-term operational cost and complexity
Architecture Behind Every Rixon Solution

Rixon Technology’s Zero Data Design sits at the core of the Rixon platform. Each step in the workflow is designed to process sensitive data without persisting original values. Cardholder data, personal identifiers, and credentials are immediately translated into governed pseudonymized tokens, ensuring raw sensitive values are not persistently retained or reconstructable.
Governed tokens can be securely stored, transmitted, and processed within the client’s technology ecosystem, reducing compliance scope, limiting breach exposure, and enabling secure payment operations across regions with complex regulatory requirements.
Security That Scales at the Speed of Payments
PCI Level 1
SOC Type 2
NIST 800-171
HIPPA
GDPR
CCPA
PCI Level 1
SOC Type 2
HIPPA
NIST 800-171
GDPR
CCPA
Why These Outcomes Are Possible
No Vaults
No persistence or failure points.
Rixon protects sensitive data without ever storing it. Our stateless tokenization removes dependency on centralized storage systems so your operations stay fast, available, and free from single points of failure.
No Keys
No rotation, theft or insider escalation.
Traditional tokenization depends on keys that must be created, rotated, and secured. Rixon eliminates the entire key management layer, reducing operational drag and stopping insider misuse before it becomes a threat.
No Storage
Nothing to breach. Nothing to steal.
Rixon's solution replaces sensitive data instantly with secure non-reversible tokens. With nothing retained in your systems, there is no data to compromise and meeting protection or compliance requirements becomes far easier.
Measured Results. Real-World Proof.
Rixon’s stateless tokenization model reduces breach exposure, streamlines compliance, and lowers long term operating costs while keeping high volume payment flows fast and uninterrupted.
AI powered monitoring and 99.999% uptime deliver nonstop protection and deep visibility across your stack, maintaining resilience even during peak transaction surges.
Up to 70% PCI Scope Reduction
28% Reduction in Fraud Loss Exposure
30–40% Lower TCO
2.5M+ TPS / <1 ms Latency
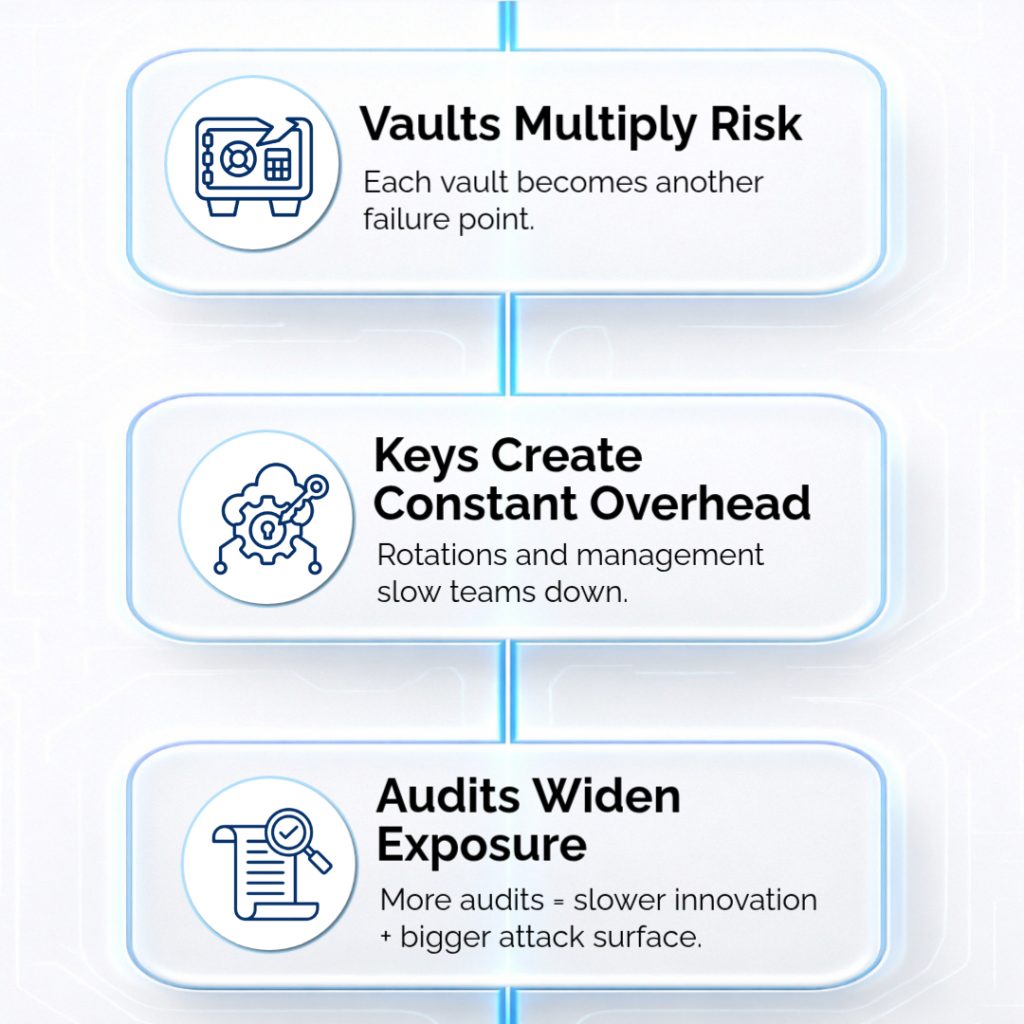
Legacy Payment Security Can’t Keep Up
Billions of mobile and QR transactions move every second. Vaults, keys, and rigid vendor ecosystems can’t keep pace with a world built on instant payments, real-time data, and AI-driven automation.
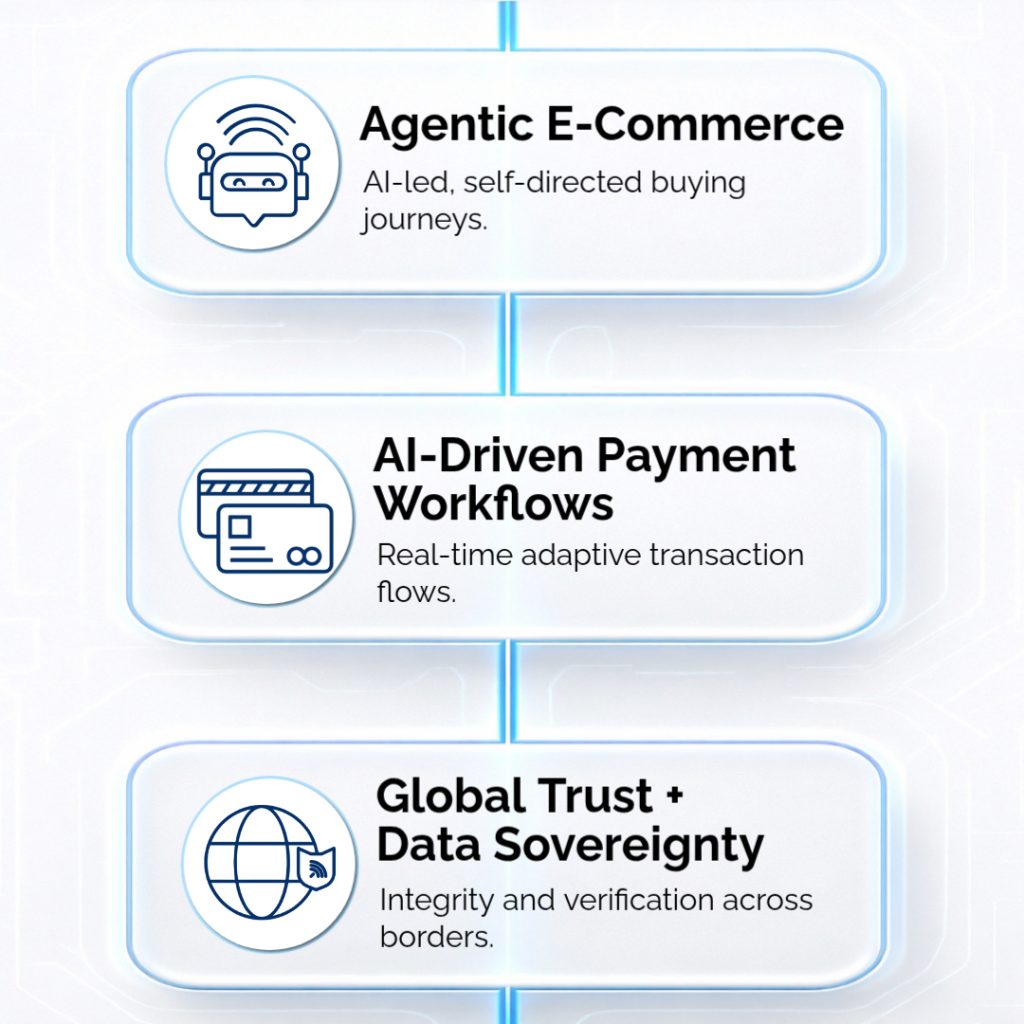
What Modern Payments Now Require
Today’s payment systems are moving faster than ever. Customers expect instant transactions, real-time decisions and smooth experiences that work across borders. They want a payment flow that stays secure, adapts on its own and does not slow them down. The reality is simple. Modern payments need intelligence, automation and trust built in from the start. Anything less cannot keep up with the pace of today’s economy.
Legacy architecture can’t deliver real-time protection in a real-time economy. Meanwhile, fraud is rising and regulations keep tightening.
PCI DSS 4.0, GDPR, LGPD, APPI, India’s DPDP Act, and others now demand local control and faster response times.
FAQ's
No. While commonly applied to payment and financial transactions, vaultless, keyless tokenization can also be used to protect other forms of sensitive data where real-time performance and reduced data exposure are required.
Vaultless, keyless tokenization reduces breach risk by eliminating the storage of sensitive data and the use of encryption keys that attackers typically target. Because no original data, vaults, or keys exist to compromise, the attack surface is significantly reduced, even if surrounding systems are breached.
No. Vaultless, keyless tokenization is designed to remove sensitive data from environments, but it works best as part of a layered security strategy that includes access controls, monitoring, and governance appropriate to the system and regulatory environment.
Vault and key systems store sensitive data or cryptographic secrets, which create latency and breach risk. Rixon uses a stateless model that transforms data without retaining it, eliminating vault lookups, key rotation, and storage dependencies. This keeps performance high while removing the primary targets attackers rely on.
Yes. Rixon is API-first and drops into your existing flows without requiring architectural changes. It works alongside your current encryption, gateways, fraud tools, and orchestration layers so you can modernize security without replacing the systems your business already depends on.
By removing sensitive data from your environment, Rixon reduces regulatory exposure and simplifies audits. Region-bound detokenization, sovereign processing paths, and full audit trails help organizations maintain compliance across jurisdictions while minimizing scope and operational overhead.
Yes. Rixon’s architecture is built for high throughput and low latency. With autoscaling, no vault dependencies, and 99.99999 percent uptime, the platform maintains consistent speed and reliability even during global peak traffic or rapid transaction surges.
Rixon’s Zero Data Design means zero sensitive data at rest. Data may pass through the system to complete a transaction, but regulated data such as card numbers, personal identifiers, and security secrets are never stored or retained. This leaves no usable data behind, even if infrastructure is compromised.
Any organization handling payments or regulated personal data benefits from eliminating stored sensitive data. Rixon is used by fintechs, digital wallets, neobanks, cross-border processors, B2B payment platforms, payroll systems, and enterprises that need fast, compliant, globally scalable data protection.
No. While commonly applied to payment and financial transactions, vaultless, keyless tokenization can also be used to protect other forms of sensitive data where real-time performance and reduced data exposure are required.
Vaultless, keyless tokenization reduces breach risk by eliminating the storage of sensitive data and the use of encryption keys that attackers typically target. Because no original data, vaults, or keys exist to compromise, the attack surface is significantly reduced, even if surrounding systems are breached.
No. Vaultless, keyless tokenization is designed to remove sensitive data from environments, but it works best as part of a layered security strategy that includes access controls, monitoring, and governance appropriate to the system and regulatory environment.
Vault and key systems store sensitive data or cryptographic secrets, which create latency and breach risk. Rixon uses a stateless model that transforms data without retaining it, eliminating vault lookups, key rotation, and storage dependencies. This keeps performance high while removing the primary targets attackers rely on.
Yes. Rixon is API-first and drops into your existing flows without requiring architectural changes. It works alongside your current encryption, gateways, fraud tools, and orchestration layers so you can modernize security without replacing the systems your business already depends on.
By removing sensitive data from your environment, Rixon reduces regulatory exposure and simplifies audits. Region-bound detokenization, sovereign processing paths, and full audit trails help organizations maintain compliance across jurisdictions while minimizing scope and operational overhead.
Yes. Rixon’s architecture is built for high throughput and low latency. With autoscaling, no vault dependencies, and 99.99999 percent uptime, the platform maintains consistent speed and reliability even during global peak traffic or rapid transaction surges.
